Today, DarkSide ransomware operation broke the news that allegedly law enforcement seized their servers and transferred all their cryptocurrency funds to another wallet.
A threat actor known as “UNKN,” who is a representative of the REvil ransomware gang, shared the news in a forum post. It was Recorded Future researcher Dmitry Smilyanets who first discovered it on the Exploit hacking forum.
Unkn reposted a message allegedly from DarkSide that explains how the gang lost access to their websites:
“Since the first version, we have promised to speak honestly and openly about problems. A few hours ago, we lost access to the public part of our infrastructure, namely: Blog, Payment server, DOS servers. Now these servers are unavailable via SSH, the hosting panels are blocked. Hosting support, apart from information “at the request of law enforcement agencies”, does not provide any other information.
Also a few hours after the withdrawal, funds from the payment server (ours and clients’) were withdrawn to an unknown address.”
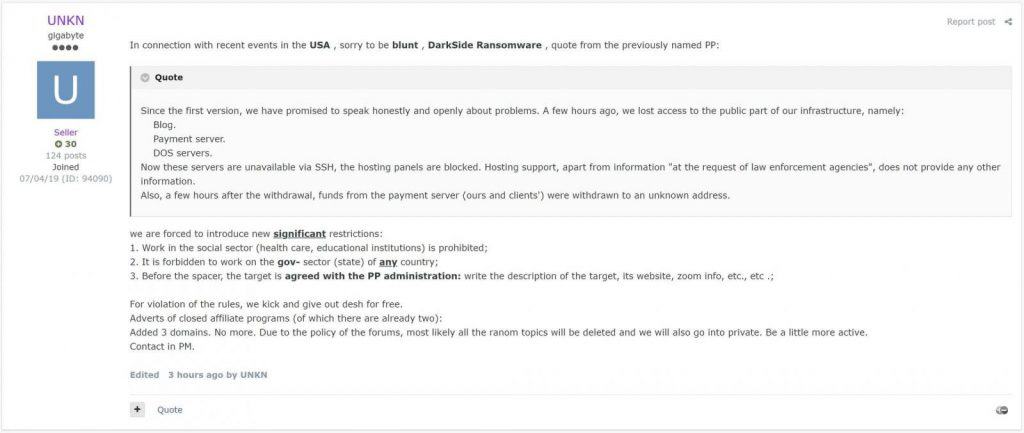
Forum post by UKNK about DarkSide seizure. Source: Dmitry Smilyanet
Just the previous day, President Biden said in a White House press conference that countries, where ransomware networks are hosted, must shut them down. DarkSide is attributed to Russian-speaking hackers.
“We do not believe — I emphasize, we do not believe the Russian government was involved in this attack. But we do have strong reason to believe that criminals who did the attack are living in Russia. That’s where it came from — were from Russia,” said Biden. “We have been in direct communication with Moscow about the imperative for responsible countries to take decisive action against these ransomware networks.”
Starting yesterday, the DarkSide data leak site was no longer accessible; however, the DarkSide Tor payment server is still operational, possibly because law enforcement, having seized the server, have chosen to keep it running to allow victims to get their decryptors.
There also has been speculation that it was an exit scam on the part of the DarkSide gang so that they could blame it on law enforcement and avoid paying affiliates. After all, they netted $9.4 million in ransom payments this week from Brenntag and Colonial Pipeline.







