Mercari, a Japanese public company and an online marketplace that has recently expanded into the United States and United Kingdom, has disclosed a major data breach incident. The company confirmed it has become another victim of the Codecov supply-chain attack.
The Mercari company was the first in Japan to reach unicorn status in 2016.
As we’ve reported before, a popular code coverage tool Codecov had been compromised by hackers in a supply-chain attack that has remained undtected for two months. As a result, threat actors exfiltrated sensitive information, such as keys, tokens, and credentials from Codecov customers’ CI/CD environments which reportedly allowed them to breach hundreds of customer networks.
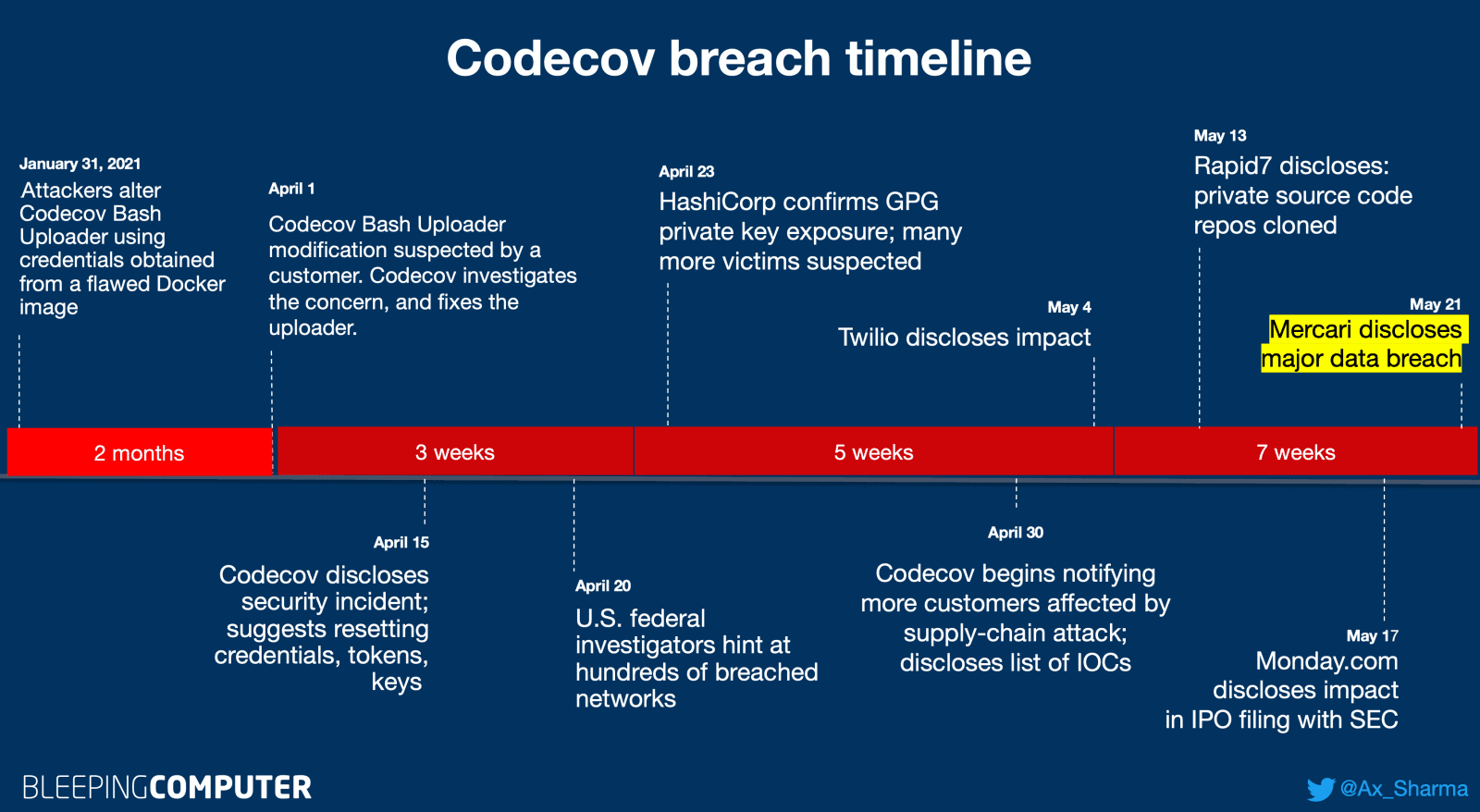
Codecov supply-chain attack timeline updated 21-May-2021 (BleepingComputer, Ax Sharma)
Today, e-commerce giant Mercari has disclosed data of its customers amounting to tens of thousands of customer records, including financial information, had been stolen by threat actors.
Mercari found out about the Codecov breach shortly after Codecov’s disclosure in mid-April and upon receiving GitHub’s notification of suspicious activity on Mercari’s repositories.
The company has conducted an investigation, and today, May 21st. The investigation showed that a third party had stolen Mercari’s authentication credentials, accessed its private repositories and source code, and accessed its systems between April 13th and April 18th. Mercari immediately revoked the compromised credentials and secrets.
On April 27, Mercari discovered that some of its customer information and source code had been illicitly accessed by unauthorized external parties. The company had multiple repositories that used the compromised Codecov Bash Uploader.
The stolen data includes:
- 17,085 sales records (bank code, branch code, account number, account holder, transfer amount)
- 7,966 records on business partners of “Mercari” and “Merpay” (names, date of birth, affiliation, e-mail address, etc. – exposed in some cases)
- 2,615 employee records (names of some present and past employees, company email addresses, employee IDs, telephone numbers, dates of birth, some contractors, and employees of external companies Mercari had interacted with)
- 217 customer service support cases (customer name, address, e-mail address, telephone number, and inquiry content)
- 6 records related to an event in May 2013.
Mercari contacted the impacted people and notified relevant authorities, including the Personal Information Protection Commission, Japan, about the attack and data breach.







