Attackers are constantly trying to upgrade and improve their methods and tools. The history repeats itself with MassLogger, an infamous Windows credential stealer, that has been recently detected siphoning credentials from applications like Outlook, Chrome, and instant messengers.
The upgraded variant of MassLogger has been uncovered by Cisco Talos experts. The firm reported attacks against users in Turkey, Latvia, and Italy. The infiltration has similarities with attacks on users in Spain, Bulgaria, Lithuania, Hungary, Estonia, and Romania in September-November 2020.
Unlike MassLogger trojan codes previously studied, the new malware version used a Microsoft proprietary online help format – Microsoft Compiled HTML Help file – to initiate the infection chain.
“This file format is typically used for Windows Help files, but it can also contain active script components, in this case, JavaScript, which launches the malware’s processes,” writes Cisco Talos in their analysis.
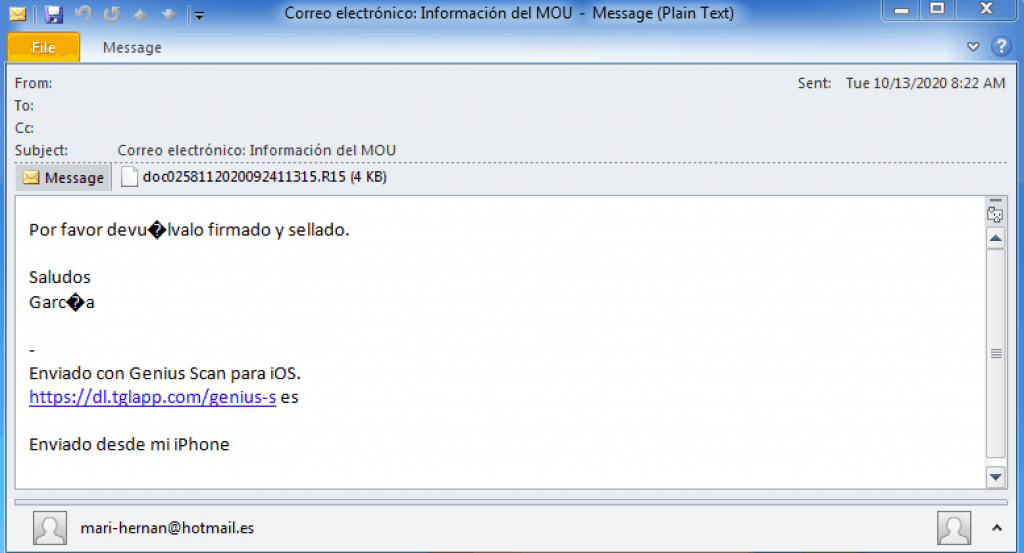
Email campaign example targeting users in Spain
The attack starts with an email with a regular-looking subject line and a RAR attachment but with an unusual filename extension. When a victim unpacks the archive, it is split into multiple parts each with “r00” extension and later with the .chm file extension. Cisco Talos experts explain this trick was necessary to bypass security measures that look for files with known extensions that attachments usually have. The attack chain eventually leads to a PowerShell script that contains the Masslogger loader.
The new MassLogger is designed for Windows and written in .NET. Once it infiltrated the victim’s machine, it is stored in memory as a buffer, compressed with gzip. The only component stored on disk is the attachment itself and the HTML help file.
“The observed campaign is almost entirely executed and present only in memory, which emphasizes the importance of conducting regular and background memory scans,” Talos’ analysts say.
The trojan would then start the exfiltration of user credentials, its targets being both home users and businesses.
So far, the MassLogger Trojan targeted Microsoft Outlook, Google Chrome, Firefox, Edge, NordVPN, FileZilla, and Thunderbird applications.
In the new attacks, hackers used several techniques of the MITRE ATT&CK framework, most notably techniques with codes T1059.001 and T1059.007 (Command and Scripting Interpreters), T1566 (Phishing), T1140 (Deobfuscate/Decode Files or Information), T1555.003 (Credentials from Web Browsers), T1497 (Virtualization/Sandbox Evasion), T1115 (Clipboard Data), T1056.001 (Keylogging), and T1048.003 (Exfiltration Over Unencrypted/Obfuscated Non-C2 Protocol).
MassLogger hunts for information like configuration options and running processes, the victim’s PC username, country ID, machine ID, and a timestamp.
Examining Indicators of Compromise (IoCs), Cisco Talos’ analysts came to a conclusion that these attacks can be linked to the past attacks that involved AgentTesla, Formbook, and AsyncRAT Trojans.
Image: Cisco Talos







