A disgruntled affiliate of the Conti ransomware gang has leaked the group’s internal tools and training materials, which included details of one of the group’s members.
Conti operates on a ransomware-as-a-service (RaaS) model that enables the core team members to manage the various components of the virus and their Tor sites, while the affiliates are responsible for finding and probing victims. Under this arrangement, the core team receives 20-30% of a ransom payment, and the affiliates get the rest.
Yesterday, a security researcher found a forum post by a likely former gang member who shared sensitive information about the gang. Among it, the IP addresses for Cobalt Strike C2 servers and an archive containing various tools and training materials.
The unhappy affiliate said in the post on a popular Russian-speaking hacking forum that he/she was only paid $1,500, while the other members of the team are making millions off of victims who paid the ransom.
“I merge you their ip-address of cobalt servers and type of training materials. 1500 $ yes, of course, they recruit suckers and divide the money among themselves, and the boys are fed with what they will let them know when the victim pays,” the affiliate wrote in the post.
The whistleblower attached images showing the configurations of the Cobalt Strike beacons and the IP addresses for command and control servers.
Experts already advised that everyone blocks the leaked IP addresses of the group to prevent attacks.
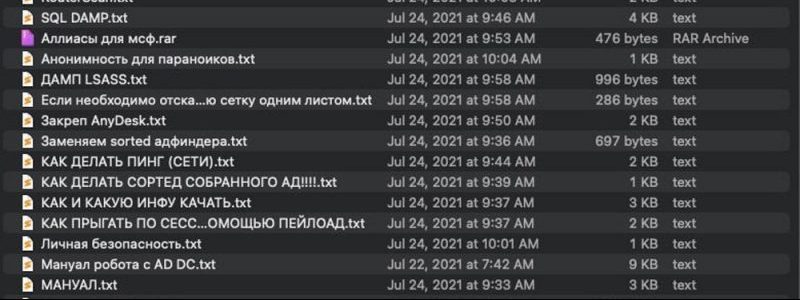
In a follow-up post, the affiliate posted an archive that contains over 111 MB of files, which included various manuals written in Russian and tools that were allegedly provided to affiliates by Conti’s core members.
Among other things, the shared folder contained a manual on deploying Cobalt Strike, numerous other text files detailing various commands, and imikatz to dump NTLM hashes.
Researchers who analyzed the leaked materials say that the training materials and tools match active Conti cases.
“We can confirm based on our active cases. This playbook matches the active cases for Conti as we see right now,” Kremez told BleepingComputer in a conversation. “By and large, it is the holy grail of the pentester operation behind the Conti ransomware “pentester” team from A-Z. The implications are huge and allow new pentester ransomware operators to level up their pentester skills for ransomware step by step.”
“The leak also shows the maturity of their ransomware organization and how sophisticated, meticulous and experienced they are while targeting corporations worldwide,” Kremez added.
The lean also provides an opportunity for security teams to ramp up their detection including insights into the group’s focus on AnyDesk persistence and Atera security software agent persistence for avoiding detections.
The leak also illustrates the vulnerability of ransomware-as-a-service operations, as a singly unhappy affiliate can expose highly valuable information and resources and thus compromise the gang.
Image: BleepingComputer