Apple has released out-of-band patches for iOS, macOS, watchOS, and Safari browsers to address a security flaw that could allow attackers to run arbitrary code on devices via malicious web content.
Out-of-band patches are emergency software modifications that are deployed by the company developer for immediate threats not waiting for the next routine update.
The patch, released outside of the tech giant’s regular monthly security cycle, impacts devices running iOS 14.4, iPadOS 14.4, macOS Big Sur, and watchOS 7.3.1 (Apple Watch Collection 3 and later), and as an update to Safari for MacBooks running macOSes Mojave and Catalina.
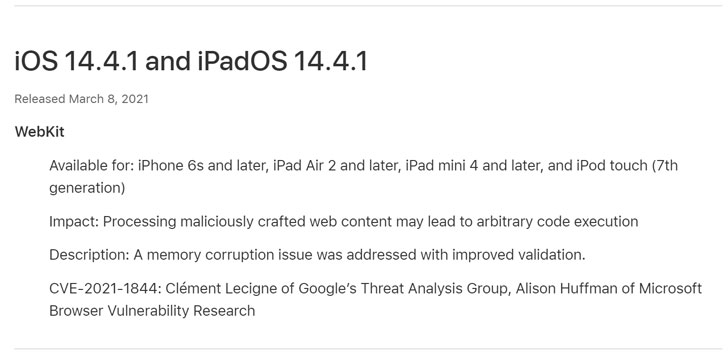
The update came following the report by Clément Lecigne of Google’s Threat Analysis Group and Alison Huffman of Microsoft Browser Vulnerability Research Tracked about a vulnerability tracked as CVE-2021-1844.
According to Apple, the flaw stems from a memory corruption that could lead to arbitrary code execution when processing specially crafted web content. The company said it fixed the vulnerability by “improved validation.”
However, there is no evidence that CVE-2021-1844 has been exploited by hackers in the wild.
Recently, Apple released another patch for three zero-day vulnerabilities tracked as CVE-2021-1782, CVE-2021-1870, and CVE-2021-1871. The flaws allowed an attacker to get high system privileges and executed code remotely. These vulnerabilities were later exploited by hackers using the “unc0ver” jailbreak tool that allowed them to unlock any iPhone model running 14.3.
It’s worth noting that Huffman was also behind the discovery of an actively exploited zero-day bug in the Chrome browser that was addressed by Google last week. But unlike the Chrome security flaw.
Even though the flaws haven’t been exploited by bad actors, they might be in the future. Users of Apple devices are advised to as soon as possible install the above updates from Apple to mitigate the risk.







