Criminals publish blog posts with titles containing popular keywords and then, Google Alerts sends the malicious blog post links to a victim’s email inbox. Although the stories are fake, the aim of the scammers is to make the user click on the link which will take them to a malicious website.
Google Alerts is a content change detection and notification service that notifies the user by email when it finds new results that match the user’s search term(s).
The blog post published by a bad actor is first indexed by Google. After that, if it matches the search query, Google Alerts sends this post to the user who would be interested in the topic of the post.
Upon clicking on the links contained in the posts sent by Google Alerts, users are redirected to malicious sites. However, if one copies the fake story’s URL and pastes in the address bar, the website will return a 404 error (page doesn’t exist).
The scheme has been detected by researchers at BeepingComputer.
“This weekend, BleepingComputer observed the fake news stories redirecting to a new campaign that states your Flash Player is outdated and then prompts you to install an updater,” states BleepingComputer.
Many users still don’t know that Adobe Flash Player has been phased out and no longer is supported by browsers and may want to update the non-existing software thinking they are installing the latest update.
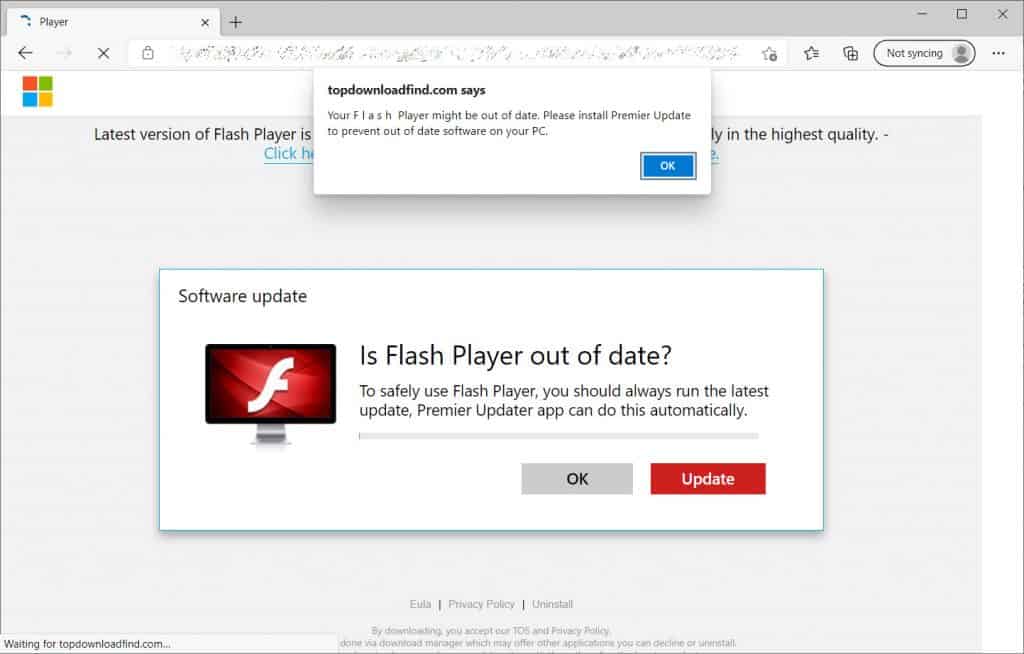
If the user clicks the “Update” button, the victim will download a setup.msi file that will install a potential malware called “One Updater.”
Although One Updater hasn’t done anything malicious yet, researchers explain this technique can be used by threat actors to deliver and execute malicious payloads in the future.
During the past week, the researchers at BeepingComputer have been studying scamming campaigns involving Google Alerts. These campaigns redirected users to web pages that showed spam notifications, offered unwanted extensions, and fake giveaways.







