Researchers Gabor Szappanos and Andrew Brandt from Sophos report that Gootkit, a well-known Javascript-based infection framework, is increasingly used to deploy an array of malware payloads in South Korea, Germany, France, and North America.
The malware delivery method has been revamped to deploy a wider range of malware besides the REvil ransomware and the Gootkit trojan.
“The developers behind Gootkit appear to have shifted resources and energy from delivering just their own financial malware to creating a stealthy, complex delivery platform for all kinds of payloads, including REvil ransomware,” said Gabor Szappanos in a today’s blog post.
Dubbed “Gootloader,” the expanded malware delivery system was first described in 2014. It is capable of carrying out covert such activities as web injection, stealing email passwords, capturing keystrokes, taking screenshots, and recording videos.
The new capabilities come after a revamp last year when Gootkit loader was repurposed to have information-stealing features when used in combination with REvil/Sodinokibi ransomware.
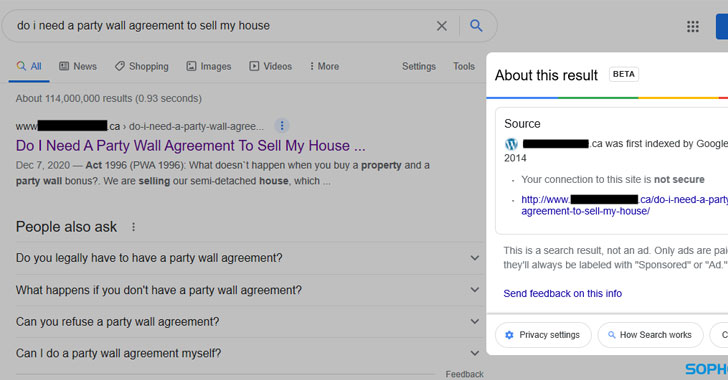
The most recent upgrade of Gootkit allows hackers to use sophisticated techniques like hosting infected ZIP archives on websites belonging to legitimate businesses that have been “SEOed” to come up at the top of the results page of a search engine.
What’s more, the search engine results point to websites that should not come up for the search query at all. The researchers explain that the hackers must have a network of websites that all work together to promote the infected pages so that they show up high in results.
“To accomplish this phase of the attack, the operators of Gootloader must maintain a network of servers hosting hacked, legitimate websites (we estimate roughly 400 such servers are in operation at any given time),” researchers write in a blog post.
Criminals target only certain geographies. For this their website code is rewritten on the go so that website visitors from other countries are shown benign web content, and the right victims are shown a page on a fake discussion forum on the topic they’re interested in.
The page on a fake forum contains a link to a ZIP file, which contains a Javascript file that injects fileless malware fetched from a remote server into memory.
“Executed either by the registry loader or the failsafe PowerShell script, the result is the same: a simple .NET loader that contains the next stage, a Delphi-based loader malware, in the form of a data blob,” the report explains.
Besides the REvil ransomware and the Gootkit Trojan, attackers have been using the Gootloader framework to deliver the Cobalt Strike post-exploitation tool in the US and the Kronos financial malware in Germany.
Researchers are not sure how the attackers gain access to the websites to serve the malicious code, but they think the attackers may have obtained the passwords by installing the Gootkit malware or somewhere purchased stolen credentials, or by leveraging some security flaws in CMS or plugins.