Researchers warn about a new malware campaign that uses a captcha to trick users into downloading the Gozi banking trojan.
MalwareHunterTeam discovered that an attacker could easily start a download of a malicious file by luring a victim with an embedded video. The YouTube video deals with a controversial topic of violence in a New Jersey women’s prison that many people will find interesting.
When clicking the play button on the video, the browser will offer to download a file named console-play.exe. This file is an executable that contains a virus. The site then displays a fake reCaptcha image, while the site will display a fake reCaptcha prompt.
Since it is a .exe file, Google Chrome automatically warns that the file may be dangerous and asks whether the user wants to ‘Keep’ or ‘Discard’ it.
The threat actors are trying to bypass the warning by displaying a fake reCaptcha image. They then ask the user to press the following buttons on their keyboard:
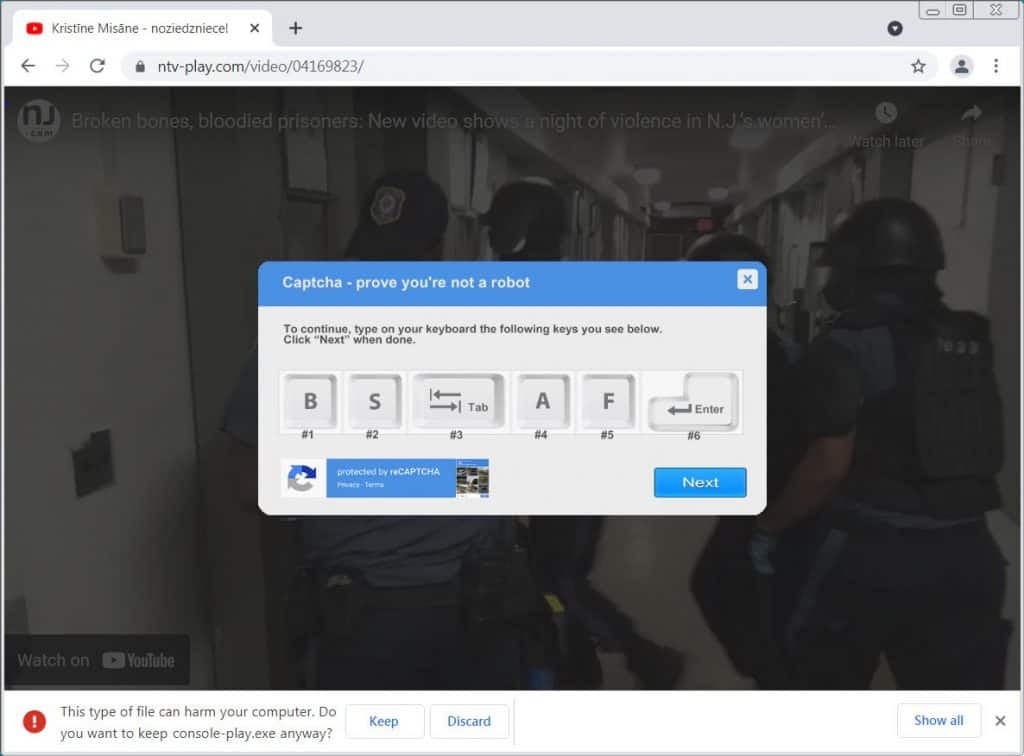
This fake captcha prompt works by tricking a user into unwittingly downloading a potentially harmful file. While pressing the Tab key, it will make the browser focus on the ‘Keep’ button, and then clicking the ‘Enter’ key will start the download.
The video will automatically play after a certain amount of time, so that not to make raise suspicions in the victim.
Some users will run the executable. And when they do, it will create a folder under %AppData%\Bouncy for .NET Helper. Except for the malicious file BouncyDotNet.exe, all other files are only decoys.
The BouncyDotNet.exe program will read the Windows Registry strings and launch PowerShell commands. It will then compile a .NET application using the built-in CSC.exe compiler that launches a DLL for the Ursnif banking trojan.
Gozi is a type of malware that enables attackers to steal account credentials and execute remote commands on a compromised computer.







