Unit 42 researchers have discovered several malicious IronPython scripts designed to load and run Turla’s malware tools on a victim’s machine.
Turla uses IronPython in an interesting way. This method is called bring your own Interpreter (BYOI) in which an interpreter (not present on the system by default) is used to run a malicious code in an interpreted programming or scripting language. It requires the use of an outside interpreter (absent from the system by default) to run malicious code in an interpreted programming or scripting language.
It were security researchers at FireEye who discovered the first malicious IronPython script last year. Earlier this year, another researcher found more new scripts from the same attacker on VirusTotal. These samples helped researchers at Unit 42 understand how the script functions and the tools used by threat actors.
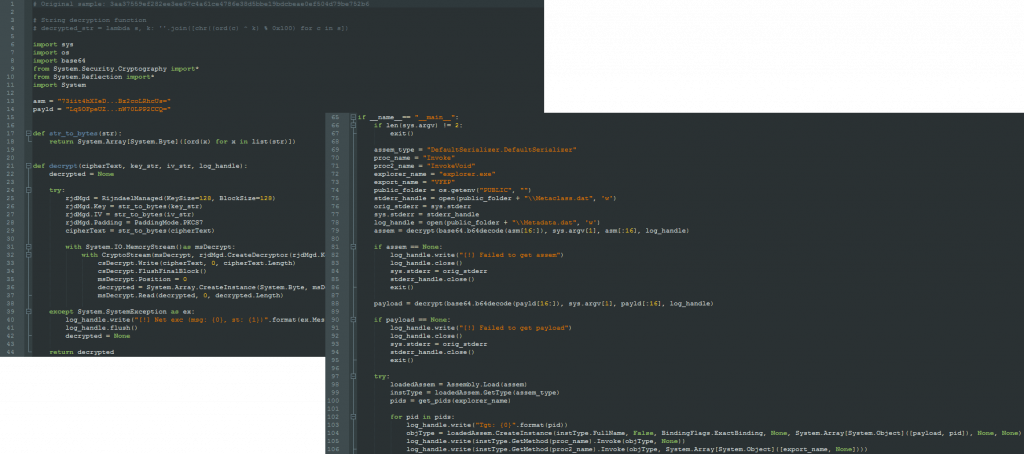
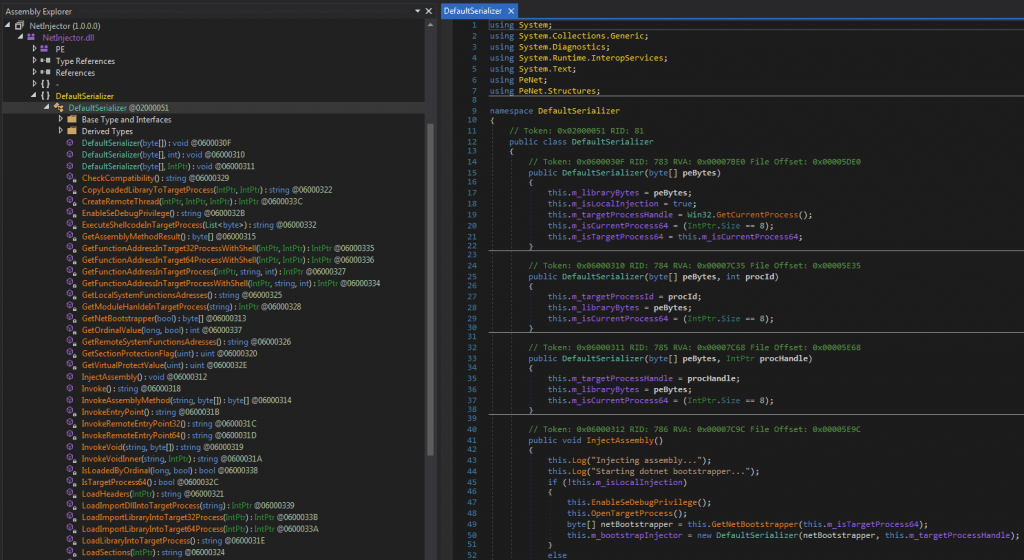
The IronPython script is only the first part of the tool. The main job of running the malware is performed by the embedded process injector. Unit 42 researchers dubbed this tool chain IronNetInjector, which is a mixture of IronPython and NetInjector.
IronNetInjector consists of an IronPython script, which contains a .NET injector and one or more payloads (can also be .NET assembly (x86/64) or native PE (x86/64)). When running the IronPython script, it will load the .NET injection program, and then inject the payload into its own or remote process.
IronPython is so attractive for malware authors because they can make use .NET framework APIs without compiling a .NET assembly with the help of an outside interpreter. The analysts detail how the IronPython scripts work and how bad actors can use them to load payloads in a blog post on the Unit 42’s website.