Researchers the GreatHorn Threat Intelligence Team reported the latest phishing scheme designed to bypass a victim’s email client defenses by changing the prefixes (aka schemes) of malicious URLs.
The latest tactic used by email phishing attackers doesn’t rely on misspelled words in the URL nor similarly looking ones – a common practice used by cybercriminals to induce the user to open the malicious link. Instead, the researchers saw malicious URLs that start with “http:/\” instead of normal “http://” with the main body of the URL remaining the same.
“The URLs don’t fit the ‘known bad’ profiles developed by simple email scanning programs, allowing them to slip through undetected,” the GreatHorn Threat Intelligence Team explained in their report.
At the same time, most browsers ignore the prefixes, because they are always the same, and take a user directly to the web page.
This type of attack involving malformed URL prefixes first appeared a while ago but is increasingly employed by cybercriminals. Just in January, the volume of such phishing attacks with malformed URLs increased by 5,933%, the GreatHorn researchers say.
Organizations in the following sectors are targeted more than others: pharmaceuticals, lending, general contracting and construction management, cable, mobile and high-speed broadband. In addition, bad actors target organizations that use Office 365 much more often than organizations running Google Workspace.
In the report, the researchers detail a phishing campaign in which the scammer impersonates a voicemail service and tries to make a user click on the following link:
http:/\brent.johnson.australiasnationalskincheckday.org.au//exr/brent.johnson@impacteddomain.com
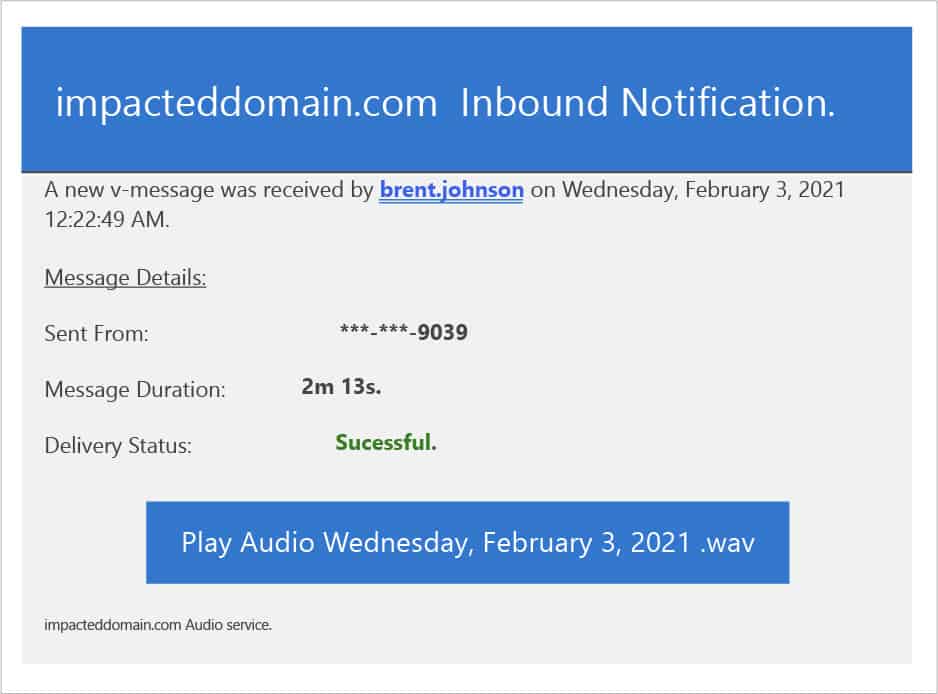
When the user clicks on the button “Play Audio…” they are redirected to a malicious website. After solving a CAPTCHA, the user sees a landing page that is identical to a Microsoft Office login page.
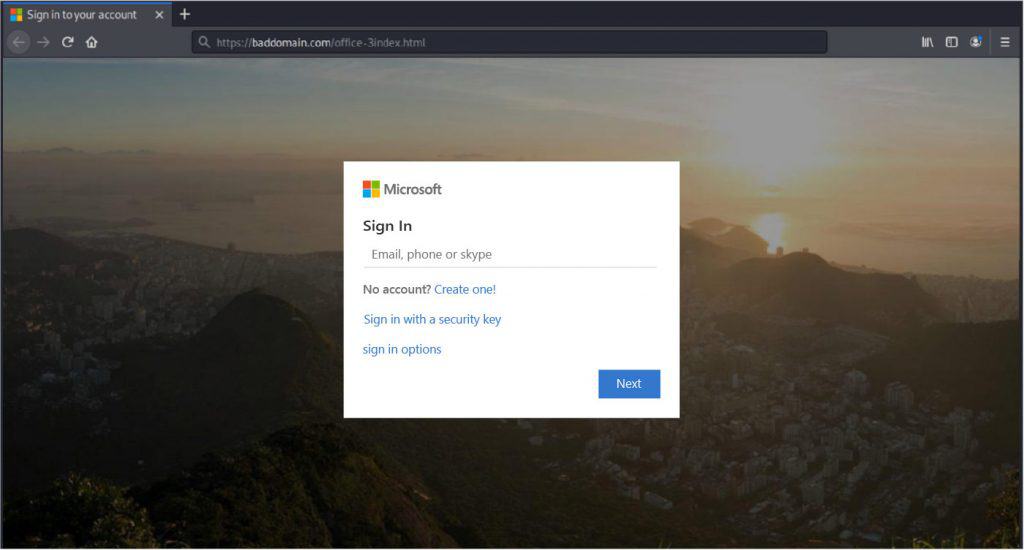
If the user enters their login details, the scammers will get what they were after.
Organizations are advised to implement solutions that do not overlook malformed URL prefixes to block credential theft attempts described above.







